Tired of looking for a good laptop under Rs. 50000? Don’t worry our experts will help you with an ideal match for your tech and office needs by suggesting one of the best affordable laptop for all your college or office needs. In the last blog of the best laptop series, we reviewed Asus Vivobook […]
The post Best Laptops under Rs. 50000: HP 15s EQ2144AU Ryzen 5 review appeared first on Computer Service Solutions.
HTTP is a Hypertext transfer protocol that facilitates the exchange of information between web pages over internet. It is a connectionless protocol that uses a request-response model. This means that when a web page sends a request, the server sends a response back with the information requested, but as a user there no way of knowing who sent the request or what information was sent although the client i.e. browser can understand what is sent or received. The information returned can be static or dynamic, and it can be self-explanatory or obscure. While it is easy to understand in terms of its purpose, it can be confusing for the non-technical user.
HTTP protocol is a session layer protocol in OSI model as it creates and manages sessions so that data can be passed in appropriate formats through presentation layer to application layer
Pre-Requisite
- MIME-type: Multipurpose Internet Mail Extension in easy words is like a guide and translator who entertain the traveler as per their interest. Technically, it is a content descriptive standard that helps browser to understand the extension of media and open the files. It also includes mail. Eg text/html, application/pdf etc.
- Different types of HTTP methods used in requests
- GET: Retrieve data or information from server
- POST: Sending data or information to server
- PUT: For modification of data on server
- DELETE: As the name suggests, deletes data on server
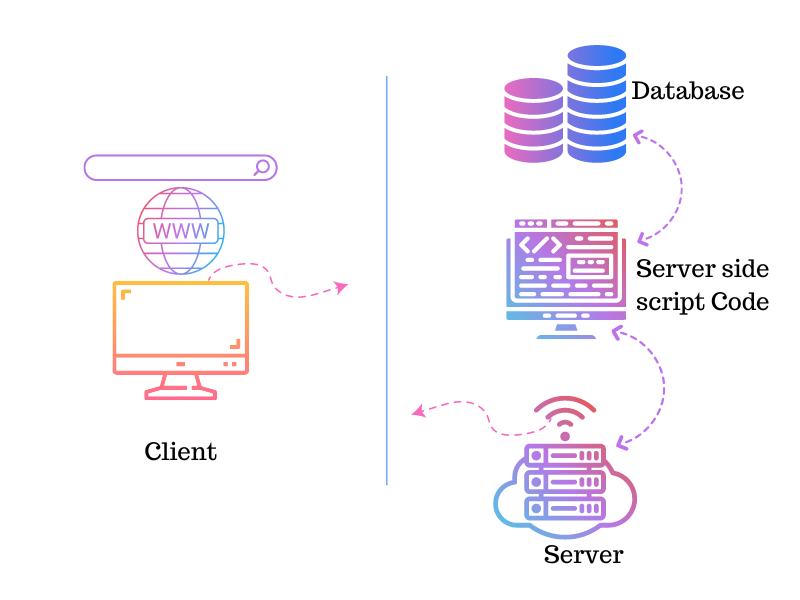
Model of HTTP Protocol and how it works
HTTP protocol is based on the model of request and response. The protocol defines the request and response process, as well as the information exchanged between them.
When user types anything on a browser act as a client, the request for HTTP gets created and sent to the server. In return, server sends the response back to the client browser.
Features of HTTP protocol
- HTTP protocol enables transmission of media of any type. The only condition is both the server and client should be able to handle the media type, and to do so, MIME type needs to be specified by the server.
- HTTP is a connectionless protocol where each time the connection is established when request is sent and disconnected when server responds to the request.
- It is a stateless protocol. Hence the information or data between different requests never gets retained.
The following diagram shows the general process of a HTTP request and response:

HTTP Request
The request seeking information shared by the browser generally contains request line, header and body (data). The http request header looks like
GET /computerservice.htm HTTP/1.1
User-Agent: Mozilla/4.0 (compatible; MSIE5.01; Windows NT)
Host: www.computerservicesolutions.in
Accept-Language: en-us
Accept-Encoding: gzip, deflate
Connection: Keep-AliveThat is a GET type of request followed by HTTP version sent through your browser to his linkedin page as host or his website. The page is a text/html type page designed via various languages and uses GZip compression to load faster. This request specifies the header and the body which is not given above in the example code contains the information best SEO freelancer in India.
HTTP response
Any HTTP response contains the HTTP status code, response header and body. It looks like:
HTTP/1.1 200 OK
Date: Sun, 25 Dec 2022 10:31:46 GMT
Server: Apache/2.2.14 (Win32)
Last-Modified: Mon, 19 Dec 2022 09:42:50 GMT
Content-Length: 84
Content-Type: text/html
Connection: ClosedIn response, the status code defines if the request is successfully answered or not if not then through server or client.
Common status codes series are:
- 1xx: Informational
- 2xx: Success
- 3xx: Redirection
- 4xx: Client side error
- 5xx: Server side error
The fields of response header are very much self explanatory.
Let us take an example to understand the whole process: You need to get the best SEO freelancer in India who is Khushank right now though, you type over browser Best SEO freelancer in India and browser takes you to this website or his LinkedIn page then
Different versions of HTTP
HTTP 0.9
The first of http version used get requests only with hypertext type responses and connections were immediately terminated
HTTP 1.0
Get, post, Head methods were used with different types of response type support. Connection gts terminated immediately
HTTP 1.1
Currently in use with more request methods like put, delete and can handle more data, compressions are supported and connections can be for long-time.
WebSockets
The WebSockets are being used by many applications because are very faster than the previous versions of HTTP as it offers bidirectional full-duplex transmission which keeps connection alive until terminated by any one of client or server.
Security issues in HTTP protocol
When you send data over the Internet, you are trusting the server to keep it safe. If the server does not properly handle the data you sent, your information could be misused or stolen. There are many ways that malicious hackers can try to breach your computer network. One possibility is to inject malicious code into a server’s web browser. Another is to use man-in-the-middle attacks to intercept your data and send it to the attacker. Another potential threat is poor host security. If an organization does not properly handle the security of its hosts (i.e., the computers that host websites), then the attacks from external hackers are also transferred through the host and might even succeed in reaching your computer network.
Various security issues or attacks because of vulnerability in HTTP leads to
- Sensitive Data Exposure, due to get parameters being used
Can be mitigated using TLS that is upgraded version of security after SSL. Use HSTS headers to mitigate such issues.
- CSRF (Cross-site request forgery)
- User with malicious intent still can intercept requests and response and play with them
But these can be mitigated using various security headers, sanitization techniques and security practices.
Also check the full-detailed article on working of SMTP Protocol and SSH protocol
The post HTTP protocol model, working and security issues with mitigations appeared first on Computer Service Solutions.
